Author: Nicholas Russo
This blog is the fourth in a series covering IP Loop Free Alternate (LFA) paths using OSPFv2. In the previous blog, we finished our discussion of “direct LFA” and the fourth inequality that describes broadcast disjointedness. The first two blogs covered the fundamental LFA inequality as well as downstream and node protection inequalities. You’ll want to read those before continuing if you haven’t already. The topology remains unchanged and is depicted below.
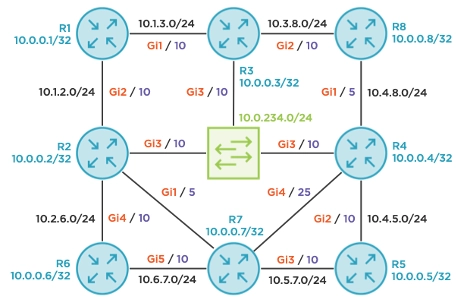
The previous blog concluded by demonstrating a gap in LFA coverage. Specifically, R2 does not have a backup path to R4’s loopback prefix of 10.0.0.4/32. Here are the outputs that prove it. The LFA coverage is only 85% (6 out of 7 possible routes) and R2’s OSPF RIB for 10.0.0.4/32 does not depict any LFAs.
R2#show ip ospf fast-reroute prefix-summary
Interface Protected Primary paths Protected paths Percent protected
All High Low All High Low All High Low
Lo0 Yes 0 0 0 0 0 0 0% 0% 0%
Gi4 Yes 1 1 0 1 1 0 100% 100% 0%
Gi1 Yes 5 2 3 2 2 0 40% 100% 0%
Gi2 Yes 2 1 1 1 1 0 50% 100% 0%
Gi3 Yes 7 3 4 2 2 0 28% 66% 0%
Area total: 15 7 8 6 6 0 40% 85% 0%
Process total: 15 7 8 6 6 0 40% 85% 0%
R2#show ip ospf rib 10.0.0.4 255.255.255.255
*> 10.0.0.4/32, Intra, cost 11, area 0
SPF Instance 78, age 11:31:48
Flags: RIB, HiPrio
via 10.0.234.4, GigabitEthernet3
Flags: RIB
LSA: 1/10.0.0.4/10.0.0.4
Source: 10.0.0.4 (area 0)
In an attempt to achieve 100% LFA coverage on R2, we’ll enable remote LFA (rLFA). This technology combines Multi-protocol Label Switching (MPLS) encapsulation with Label Distribution Protocol (LDP) signaling to create backup paths. Like most LFA features, it’s simple to configure but complex to understand. Be sure you understand MPLS and LDP fundamentals before continuing; you can learn about it at Pluralsight with this course.
First, we must enable MPLS throughout the network using LDP. Defining unique label ranges on each device simplifies troubleshooting. R1 will allocate local labels from the range 1000 to 1999, R2 will use 2000 to 2999, etc. As a best practice, we’ll hardcode the LDP router ID (which must be a routable IP address) to Loopback0 on each device. It is between these loopbacks that TCP-based sessions are formed to exchange MPLS labels. Last, we’ll dynamically enable LDP on all OSPF area 0 links. In our flat area 0 topology, this ensures that LDP is uniformly configured.
In a production network, you’d probably enable rLFA everywhere, both for consistency and better overall LFA coverage. However, in our lab topology, the other routers already have 100% LFA coverage using direct LFA, so rLFA is technically only necessary on R2. We’ll limit the configuration to R2 to stay focused. Notice that rLFA is enabled on a per-area basis and (in theory) supports multiple encapsulation types, but only MPLS/LDP is supported today on Cisco IOS-XE. Finally, we’ll configure R5 to dynamically accept targeted LDP hellos from any other router. This step seems odd, but I promise I’ll explain it soon.
# All routers
mpls label range 1000 1999 ! different ranges per device
mpls ldp router-id Loopback0 force
router ospf 1
mpls ldp autoconfig area 0
# R2 configuration
router ospf 1
fast-reroute per-prefix remote-lfa area 0 tunnel mpls-ldp
# R5 configuration
mpls ldp discovery targeted-hello accept
With rLFA configured, you’ll notice that R2 and R5 suddenly form an LDP neighbor relationship. They aren’t directly connected, but according to the output below, R2 sent a targeted hello from 10.0.0.2 to 10.0.0.5. R5 was configured to accept these hellos, enabling it to dynamically respond to R2. Checking R2’s LFA coverage, we now see 100% coverage, implying that 10.0.0.4/32 is now protected.
R2#show mpls ldp neighbor 10.0.0.5
Peer LDP Ident: 10.0.0.5:0; Local LDP Ident 10.0.0.2:0
TCP connection: 10.0.0.5.12913 - 10.0.0.2.646
State: Oper; Msgs sent/rcvd: 36/37; Downstream
Up time: 00:13:12
LDP discovery sources:
Targeted Hello 10.0.0.2 -> 10.0.0.5, active
Addresses bound to peer LDP Ident:
10.4.5.5 10.5.7.5 10.0.0.5
R2#show ip ospf fast-reroute prefix-summary
Interface Protected Primary paths Protected paths Percent protected
All High Low All High Low All High Low
Lo0 Yes 0 0 0 0 0 0 0% 0% 0%
Gi4 Yes 1 1 0 1 1 0 100% 100% 0%
Gi1 Yes 5 2 3 2 2 0 40% 100% 0%
Gi2 Yes 2 1 1 1 1 0 50% 100% 0%
Gi3 Yes 7 3 4 3 3 0 42% 100% 0%
Area total: 15 7 8 7 7 0 46% 100% 0%
Process total: 15 7 8 7 7 0 46% 100% 0%
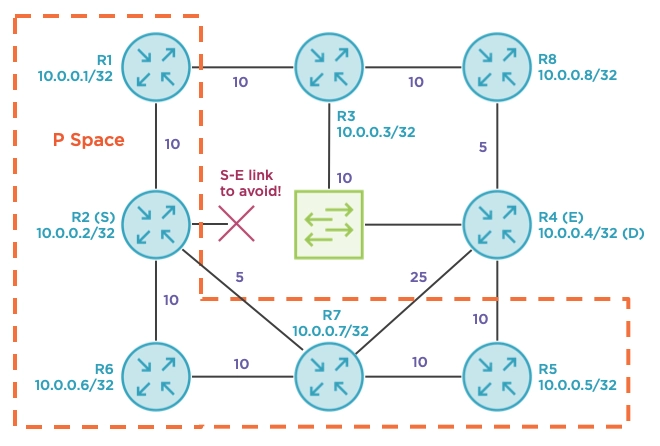
All of this seems very confusing. How did this LDP session suddenly provide protection to R4’s loopback? More importantly, what’s the topological relevance of R5? The brilliance of rLFA lies within the concept of P and Q spaces. The P space is the collection of routers that R2 (S) can reach without transiting the protected link between R2 and R4 (S-E). For example, the path from R2 to R1 does not traverse the S-E link, therefore R1 is in the P-space. The same is true for R6, R7, and R5; R2’s shortest path to each of these devices does not transit the broadcast network (S-E), which is the link we want to avoid. R3 and R8 are not in the P-space because R2’s shortest path to these nodes traverses the S-E link. Most P space routers are closer to S than to D.
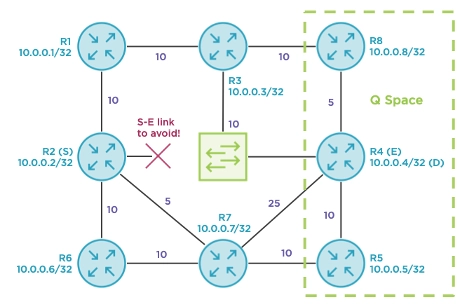
The Q space is the collection of routers that can reach 10.0.0.4/32 (D) without traversing the primary link between R2 and R4 (S-E). By this definition, R8 is in the Q space, given that its shortest path to R4’s loopback uses the connected R8-R4 link. The same is true for R5. No other nodes are in the Q space because they would all traverse the broadcast network that we are trying to protect. Most Q space routers are closer to D than to S.
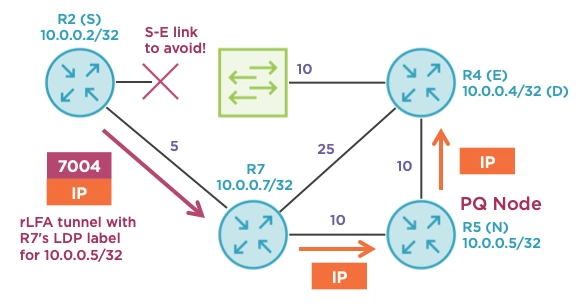
When a router exists in both the P and Q spaces, we call this a PQ node. This router can be reached by S and can reach D without traversing the S-E link. These devices tend to be roughly midway between S and D and serve as MPLS tunnel endpoints. If R2 can safely deliver packets to R5, R5 is guaranteed not to loop them back through R2 (S) nor across the protected link (S-E) when destined to 10.0.0.4/32 (D). R2 computed the P and Q spaces, identified R5 as the PQ node (some networks may have multiple PQ nodes), and created an LDP session towards it. The PQ node is comparable to a candidate next-hop (N) in the context of direct LFA inequalities except that is not directly connected.

Before discussing the MPLS mechanics, let’s explore the LFA SPF debugging. The output is verbose and difficult to control, but it does demonstrate the construction of the P space. Unfortunately, it makes no mention of the Q space nor does it clarify which S-E link is being evaluated for each P space addition. Here’s a subset of that output, and towards the bottom, we see that 10.0.0.5 (R5) is added to the P space using 10.0.0.7 (R7) as the next-hop node.
R2#debug ip ospf fast-reroute spf detail
OSPF Loop-free FastReroute SPF computation debugging is on with detail
R2#clear ip ospf force-spf
OSPF-1 FRSPF: Adding to SPF tree router LSA 10.0.0.5, dist 10
OSPF-1 FRSPF: Processing link type 3, id 10.0.0.5, data 255.255.255.255, metric 1
OSPF-1 FRSPF: Processing link type 1, id 10.0.0.7, data 10.5.7.5, metric 10
OSPF-1 FRSPF: Can't improve distance 0 with 20
OSPF-1 FRSPF: Processing link type 3, id 10.5.7.0, data 255.255.255.0, metric 10
OSPF-1 FRSPF: Processing link type 1, id 10.0.0.4, data 10.4.5.5, metric 10
OSPF-1 FRSPF: Improve LSA type 1, id 10.0.0.4, adv 10.0.0.4 on the candidate list with distance 20
OSPF-1 FRSPF: Processing link type 3, id 10.4.5.0, data 255.255.255.0, metric 10
OSPF-1 FRSPF: Add router 10.0.0.5 to P-space via neighbor 10.0.0.7
OSPF-1 FRSPF: Refreshing first hop via 10.2.7.7 GigabitEthernet1
An easier way to test this on your own is to use traceroute. Let’s quickly cover three examples for brevity. We know that R5 is a PQ node and is therefore in both the P and Q spaces. This means that R2 (S) should be able to reach R5 and that R5 should be able to reach 10.0.0.4/32 (D) without traversing the protected link (S-E). The traceroute outputs below prove this.
R2#traceroute 10.0.0.5 source 10.0.0.2
Type escape sequence to abort.
Tracing the route to 10.0.0.5
VRF info: (vrf in name/id, vrf out name/id)
1 10.2.7.7 [MPLS: Label 7004 Exp 0] 2 msec 1 msec 1 msec
2 10.5.7.5 2 msec 2 msec 2 msec
R5#traceroute 10.0.0.4 source 10.0.0.5
Type escape sequence to abort.
Tracing the route to 10.0.0.4
VRF info: (vrf in name/id, vrf out name/id)
1 10.4.5.4 1 msec 1 msec 1 msec
R8 is in the Q space but not the P space as discussed previously. R2 (S) traverses the broadcast network to reach it, but R8 can reach 10.0.0.4/32 (D) without using the broadcast network. Note that there is a concept of "extended P space" which relaxes the P space rules a bit, but that's a discussion for another day. Focusing on the core P and Q concepts is more educationally useful at present.
R2#traceroute 10.0.0.8 source 10.0.0.2
Type escape sequence to abort.
Tracing the route to 10.0.0.8
VRF info: (vrf in name/id, vrf out name/id)
1 10.0.234.4 [MPLS: Label 4006 Exp 0] 2 msec 1 msec 1 msec
2 10.4.8.8 2 msec 2 msec 2 msec
R8#traceroute 10.0.0.4 source 10.0.0.8
Type escape sequence to abort.
Tracing the route to 10.0.0.4
VRF info: (vrf in name/id, vrf out name/id)
1 10.4.8.4 2 msec 2 msec 1 msec
Last, R6 is in the P space but not the Q space. R2 (S) can reach R6 while avoiding the protected link but R6 must traverse that S-E link to reach 10.0.0.4/32 (D).
R2#traceroute 10.0.0.6 source 10.0.0.2
Type escape sequence to abort.
Tracing the route to 10.0.0.6
VRF info: (vrf in name/id, vrf out name/id)
1 10.2.6.6 2 msec 0 msec 1 msec
R6#traceroute 10.0.0.8 source 10.0.0.6
Type escape sequence to abort.
Tracing the route to 10.0.0.8
VRF info: (vrf in name/id, vrf out name/id)
1 10.2.6.2 [MPLS: Label 2006 Exp 0] 2 msec 2 msec 2 msec
2 10.0.234.4 [MPLS: Label 4006 Exp 0] 1 msec 1 msec 2 msec
3 10.4.8.8 3 msec 2 msec 2 msec
Next, let’s discuss the MPLS mechanics of rLFA. Enabling LFA RIB debugging, you’ll see a familiar set of output. The ACL limits the debug to only 10.0.0.4/32 (D) on R2 (S) and I’ve separated the output into four stanzas. The first three reveal that direct LFAs do not exist to D, which we saw in the previous blog. Each of them clearly fails to satisfy Inequality 1. The last stanza shows rLFA coming to the rescue. It creates an MPLS tunnel from R2 (S) to the PQ node of R5, but doesn’t tell us much else.
# R2 configuration
ip access-list standard 4
10 permit 10.0.0.4
R2#debug ip ospf fast-reroute rib 4
OSPF Loop-free FastReroute local RIB debugging is on for access list 4
R2#clear ip ospf force-spf
OSPF-1 FRRIB: Refreshing router 10.0.0.4 route: intra-area path, distance 20
OSPF-1 FRRIB: Add to LRIB repair path 10.0.0.4/255.255.255.255 via neighbor 10.0.0.6,
area 0, type Intra, D(N,D)=21, ext2 metric 0
OSPF-1 FRRIB: Not an LFA; D(N,D)=21, D(N,S)=10, D(S,D)=11
OSPF-1 FRRIB: Refreshing router 10.0.0.4 route: intra-area path, distance 15
OSPF-1 FRRIB: Add to LRIB repair path 10.0.0.4/255.255.255.255 via neighbor 10.0.0.7,
area 0, type Intra, D(N,D)=16, ext2 metric 0
OSPF-1 FRRIB: Not an LFA; D(N,D)=16, D(N,S)=5, D(S,D)=11
OSPF-1 FRRIB: Refreshing router 10.0.0.4 route: intra-area path, distance 20
OSPF-1 FRRIB: Add to LRIB repair path 10.0.0.4/255.255.255.255 via neighbor 10.0.0.1,
area 0, type Intra, D(N,D)=21, ext2 metric 0
OSPF-1 FRRIB: Not an LFA; D(N,D)=21, D(N,S)=10, D(S,D)=11
OSPF-1 FRRIB: RmtLFA analyzing route 10.0.0.4/32
OSPF-1 FRRIB: For primary path via 10.0.234.4 GigabitEthernet3
RmtLFA adds repair path via 10.0.0.5 MPLS-Remote-Lfa1
OSPF-1 FRRIB: Adding repair path after path via 10.0.234.4 GigabitEthernet3, flags (RIB)
OSPF-1 FRRIB: Finished processing RmtLFA, added 1 repair paths
The debug indicates that the backup interface is "MPLS-Remote-Lfa1" and we can query the OSPF LFA process for more information. The "remote-lfa tunnels" command reveals the tunnel endpoint of 10.0.0.5 (PQ node) as well as the primary next-hop (E) being protected, which is 10.0.234.4 on R4. The OSPF RIB now has an LFA via R5 via this rLFA tunnel. Notice the label count is 1, implying that only a single MPLS label is necessary at present.
R2#show ip ospf fast-reroute remote-lfa tunnels
Interface MPLS-Remote-Lfa1, if-number 16
Tunnel type: MPLS-LDP
Tailend router ID: 10.0.0.5
Termination IP address: 10.0.0.5
Outgoing interface: GigabitEthernet1
First hop gateway: 10.2.7.7
Tunnel metric: 10
Protects:
10.0.234.4 GigabitEthernet3, total metric 20
R2#show ip ospf rib 10.0.0.4 255.255.255.255
*> 10.0.0.4/32, Intra, cost 11, area 0
SPF Instance 79, age 11:39:46
Flags: RIB, HiPrio
via 10.0.234.4, GigabitEthernet3
Flags: RIB
LSA: 1/10.0.0.4/10.0.0.4
Source: 10.0.0.4 (area 0)
repair path via 10.0.0.5, MPLS-Remote-Lfa1 cost 20, Lbl cnt 1
Flags: RIB, Repair, IntfDj, CostWon
LSA: 1/10.0.0.4/10.0.0.4
How can we find the label value? Let’s query the IP FIB internal details to see what the outbound encapsulation process reports. Towards 10.0.0.4/32 (D), the primary next-hop (E) uses regular IP out of a directly connected interface. The repair path via the rLFA interface pushes label 7004 first, then sends the MPLS packet to 10.2.7.7, which is R7. Checking the Label Information Base (LIB), R2 reports that label 7004 was learned from R7 and represents an LSP towards R5’s loopback prefix.
R2#show ip cef 10.0.0.4/32 internal | begin output chain
output chain:
label [implicit-null|5003]-(local:2002)
FRR Primary (0x80007F287EE91870)
<primary: IP adj out of GigabitEthernet3, addr 10.0.234.4 7F287E9DEB08>
<repair: TAG midchain out of MPLS-Remote-Lfa1 7F287900C3B8
label 7004
TAG adj out of GigabitEthernet1, addr 10.2.7.7 7F287900CEA8>
R2#show mpls ldp bindings remote-label 7004
lib entry: 10.0.0.5/32, rev 10
remote binding: lsr: 10.0.0.7:0, label: 7004
When R7 receives label 7004 on ingress, it removes this label due to penultimate hop popping (PHP), then forwards the plain IP packet to R5. This short MPLS tunnel prevents R7 from consulting its IP FIB and incorrectly looping traffic for 10.0.0.4/32 (D) back towards R2 (S). Remember, R7 is not in the Q space, and therefore relies on the S-E link for transport to D. Instead, R7 consults its LFIB and tunnels traffic for 10.0.0.4/32 (D) towards R5 (PQ node) instead. Having received this plain IP packet, R5 performs an IP FIB lookup and routes the packet to R4 normally.
R7#show mpls forwarding-table labels 7004
Local Outgoing Prefix Bytes Label Outgoing Next Hop
Label Label or Tunnel Id Switched interface
7004 Pop Label 10.0.0.5/32 15369 Gi3 10.5.7.5
R5#show ip route ospf | include 10.0.0.4/32
O 10.0.0.4/32 [110/11] via 10.4.5.4, 13:28:34, GigabitEthernet2
Note that R4’s (S) return path to 10.0.0.2/32 (D) on R2 is protected by a direct LFA via R7 (N). We didn’t need rLFA on R4; this is often the result of asymmetric topologies with respect to link connectivity and IGP costs. Only the unidirectional R2-R4 link needed rLFA protection!
R4#show ip route 10.0.0.2 255.255.255.255
Routing entry for 10.0.0.2/32
Known via "ospf 1", distance 110, metric 11, type intra area
Last update from 10.0.234.2 on GigabitEthernet3, 12:37:04 ago
Routing Descriptor Blocks:
* 10.0.234.2, from 10.0.0.2, 12:37:04 ago, via GigabitEthernet3
Route metric is 11, traffic share count is 1
Repair Path: 10.4.7.7, via GigabitEthernet4
Last, consider what happens if we significantly increase the cost of all links connecting to R4, excluding the broadcast network. The snippet below illustrates these temporary cost adjustments.
# R5 configuration
interface GigabitEthernet2
ip ospf cost 35
# R8 configuration
interface GigabitEthernet1
ip ospf cost 35
# R4 configuration
interface GigabitEthernet1
ip ospf cost 35
interface GigabitEthernet2
ip ospf cost 35
Recall that R5 and R8 were in the Q space prior to these cost adjustments. Now, neither R5 nor R8 are in the Q space. Their shortest paths to 10.0.0.4/32 (D) now route through the protected broadcast network (S-E). The P and Q spaces never overlap, so there are zero PQ nodes in the network.

As a result, R2 (S) can no longer protect the path to R4’s loopback (D) as indicated in the OSPF RIB entry. When routers closer to D have a single low cost link but are otherwise surrounded by high cost links, it makes Q space membership much less likely, ultimately leading to worse rLFA coverage. Plan your costs accordingly!
R5#traceroute 10.0.0.4 source 10.0.0.5
Type escape sequence to abort.
Tracing the route to 10.0.0.4
VRF info: (vrf in name/id, vrf out name/id)
1 10.5.7.7 [MPLS: Label 7003 Exp 0] 2 msec 2 msec 2 msec
2 10.2.7.2 [MPLS: Label 2002 Exp 0] 1 msec 1 msec 2 msec
3 10.0.234.4 2 msec 2 msec 2 msec
R8#traceroute 10.0.0.4 source 10.0.0.8
Type escape sequence to abort.
Tracing the route to 10.0.0.4
VRF info: (vrf in name/id, vrf out name/id)
1 10.3.8.3 [MPLS: Label 3002 Exp 0] 2 msec 1 msec 1 msec
2 10.0.234.4 2 msec 2 msec 1 msec
R2#show ip ospf rib 10.0.0.4 255.255.255.255
*> 10.0.0.4/32, Intra, cost 11, area 0
SPF Instance 97, age 00:02:11
Flags: RIB, HiPrio
via 10.0.234.4, GigabitEthernet3
Flags: RIB
LSA: 1/10.0.0.4/10.0.0.4
Source: 10.0.0.4 (area 0)
In summary, remote LFA improves coverage over direct LFA by using MPLS encapsulation to tunnel traffic from the source router to a designated midpoint router, called the PQ node. This technique guarantees loop-free forwarding towards the final destination and often provides better coverage than direct LFA alone. Like direct LFA, remote LFA is not a magic trick and does not guarantee 100% coverage. It is still topology-dependent as demonstrated at the end of this blog. Is there a topology-independent way of computing LFAs to guarantee 100% coverage?
In This Series:
- Introducing IP Loop Free Alternates (LFA) with OSPFv2
- Exploring Downstream and Node-protecting IP LFAs using OSPFv2
- Examining Broadcast Disjointedness and IP LFA Coverage with OSPFv2
- Improving IP LFA Coverage using Remote LFA with MPLS and OSPFv2 (this article)
- Maximizing IP LFA Coverage using Topology-independent LFA and Segment Routing
Reference Configurations:
# R1
version 17.3
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
platform console serial
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no ip icmp rate-limit unreachable
!
!
!
!
!
!
!
no ip domain lookup
ip domain name lab.local
!
!
mpls label range 1000 1999
!
!
interface Loopback0
ip address 10.0.0.1 255.255.255.255
!
interface GigabitEthernet1
ip address 10.1.3.1 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet2
ip address 10.1.2.1 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
!
router ospf 1
fast-reroute per-prefix enable area 0 prefix-priority high
fast-reroute keep-all-paths
network 0.0.0.0 255.255.255.255 area 0
mpls ldp autoconfig area 0
!
!
ip ssh version 2
!
!
!
!
mpls ldp router-id Loopback0 force
!
!
end
# R2
version 17.3
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
platform console serial
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no ip icmp rate-limit unreachable
!
!
!
!
!
!
!
no ip domain lookup
ip domain name lab.local
!
!
mpls label range 2000 2999
!
interface Loopback0
ip address 10.0.0.2 255.255.255.255
!
interface GigabitEthernet1
ip address 10.2.7.2 255.255.255.0
ip ospf network point-to-point
ip ospf cost 5
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet2
ip address 10.1.2.2 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
ip address 10.0.234.2 255.255.255.0
ip ospf network broadcast
ip ospf priority 0
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet4
ip address 10.2.6.2 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
!
router ospf 1
fast-reroute per-prefix enable area 0 prefix-priority high
fast-reroute per-prefix remote-lfa area 0 tunnel mpls-ldp
fast-reroute keep-all-paths
network 0.0.0.0 255.255.255.255 area 0
mpls ldp autoconfig area 0
!
ip ssh version 2
!
!
ip access-list standard 4
10 permit 10.0.0.4
!
!
mpls ldp router-id Loopback0 force
!
!
!
end
# R3
version 17.3
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
platform console serial
!
hostname R3
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no ip icmp rate-limit unreachable
!
!
!
!
no ip domain lookup
ip domain name lab.local
!
!
!
!
mpls label range 3000 3999
!
!
!
interface Loopback0
ip address 10.0.0.3 255.255.255.255
!
interface GigabitEthernet1
ip address 10.1.3.3 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet2
ip address 10.3.8.3 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
ip address 10.0.234.3 255.255.255.0
ip ospf network broadcast
ip ospf priority 0
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
!
router ospf 1
fast-reroute per-prefix enable area 0 prefix-priority high
fast-reroute keep-all-paths
network 0.0.0.0 255.255.255.255 area 0
mpls ldp autoconfig area 0
!
ip ssh version 2
!
!
!
!
mpls ldp router-id Loopback0 force
!
!
!
end
# R4
version 17.3
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
platform console serial
!
hostname R4
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no ip icmp rate-limit unreachable
!
!
!
!
!
!
!
no ip domain lookup
ip domain name lab.local
!
!
mpls label range 4000 4999
!
!
!
!
interface Loopback0
ip address 10.0.0.4 255.255.255.255
!
interface GigabitEthernet1
ip address 10.4.8.4 255.255.255.0
ip ospf network point-to-point
ip ospf cost 5
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet2
ip address 10.4.5.4 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
ip address 10.0.234.4 255.255.255.0
ip ospf network broadcast
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet4
ip address 10.4.7.4 255.255.255.0
ip ospf network point-to-point
ip ospf cost 25
negotiation auto
no mop enabled
no mop sysid
!
!
router ospf 1
fast-reroute per-prefix enable area 0 prefix-priority high
fast-reroute per-prefix tie-break primary-path index 10
fast-reroute per-prefix tie-break interface-disjoint index 20
fast-reroute per-prefix tie-break downstream index 25
fast-reroute per-prefix tie-break lowest-metric index 30
fast-reroute per-prefix tie-break linecard-disjoint index 40
fast-reroute per-prefix tie-break broadcast-interface-disjoint index 50
fast-reroute keep-all-paths
network 0.0.0.0 255.255.255.255 area 0
mpls ldp autoconfig area 0
!
!
ip ssh version 2
!
!
!
!
mpls ldp router-id Loopback0 force
!
!
!
!
end
# R5
version 17.3
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
platform console serial
!
hostname R5
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no ip icmp rate-limit unreachable
!
!
!
!
!
!
!
no ip domain lookup
ip domain name lab.local
!
!
!
login on-success log
!
!
!
!
mpls label range 5000 5999
mpls ldp discovery targeted-hello accept
!
!
interface Loopback0
ip address 10.0.0.5 255.255.255.255
!
interface GigabitEthernet1
no ip address
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet2
ip address 10.4.5.5 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet3
ip address 10.5.7.5 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
!
router ospf 1
fast-reroute per-prefix enable area 0 prefix-priority high
fast-reroute keep-all-paths
network 0.0.0.0 255.255.255.255 area 0
mpls ldp autoconfig area 0
!
!
ip ssh version 2
!
!
!
!
mpls ldp router-id Loopback0 force
!
!
!
end
# R6
version 17.3
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
platform console serial
!
hostname R6
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no ip icmp rate-limit unreachable
!
!
!
!
!
!
!
no ip domain lookup
ip domain name lab.local
!
!
!
login on-success log
!
!
!
!
!
mpls label range 6000 6999
!
!
!
!
!
interface Loopback0
ip address 10.0.0.6 255.255.255.255
!
!
interface GigabitEthernet4
ip address 10.2.6.6 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet5
ip address 10.6.7.6 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
!
router ospf 1
fast-reroute per-prefix enable area 0 prefix-priority high
fast-reroute keep-all-paths
network 0.0.0.0 255.255.255.255 area 0
mpls ldp autoconfig area 0
!
!
ip ssh version 2
!
!
!
!
mpls ldp router-id Loopback0 force
!
!
!
!
end
# R7
version 17.3
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
platform console serial
!
hostname R7
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no ip icmp rate-limit unreachable
!
!
!
!
!
!
!
no ip domain lookup
ip domain name lab.local
!
!
!
mpls label range 7000 7999
!
!
!
!
interface Loopback0
ip address 10.0.0.7 255.255.255.255
!
interface GigabitEthernet1
ip address 10.2.7.7 255.255.255.0
ip ospf network point-to-point
ip ospf cost 5
negotiation auto
no mop enabled
no mop sysid
!
!
interface GigabitEthernet3
ip address 10.5.7.7 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet4
ip address 10.4.7.7 255.255.255.0
ip ospf network point-to-point
ip ospf cost 25
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet5
ip address 10.6.7.7 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
!
router ospf 1
fast-reroute per-prefix enable area 0 prefix-priority high
fast-reroute keep-all-paths
network 0.0.0.0 255.255.255.255 area 0
mpls ldp autoconfig area 0
!
!
ip ssh version 2
!
!
!
!
mpls ldp router-id Loopback0 force
!
!
!
end
# R8
version 17.3
service timestamps debug datetime msec
service timestamps log datetime msec
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
platform console serial
!
hostname R8
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no ip icmp rate-limit unreachable
!
!
!
!
!
!
!
no ip domain lookup
ip domain name lab.local
!
!
!
mpls label range 8000 8999
!
!
!
!
!
interface Loopback0
ip address 10.0.0.8 255.255.255.255
!
interface GigabitEthernet1
ip address 10.4.8.8 255.255.255.0
ip ospf network point-to-point
ip ospf cost 5
negotiation auto
no mop enabled
no mop sysid
!
interface GigabitEthernet2
ip address 10.3.8.8 255.255.255.0
ip ospf network point-to-point
ip ospf cost 10
negotiation auto
no mop enabled
no mop sysid
!
!
router ospf 1
fast-reroute per-prefix enable area 0 prefix-priority high
fast-reroute keep-all-paths
network 0.0.0.0 255.255.255.255 area 0
mpls ldp autoconfig area 0
!
!
ip ssh version 2
!
!
!
!
mpls ldp router-id Loopback0 force
!
!
!
end
